SSL/TLS Issues
When communicating with SharePoint Online or any other secured environment, it could happen that you trigger one of the following errors:
- Could not establish trust relationship
- The client and server cannot communicate, because they do not possess a common algorithm
- An existing connection was forcibly closed
- The underlying connection was closed: An unexpected error occurred on a send
- Token request failed
- In an Ometa web component like CM or ADM: An error has occurred
- This is a generic error message from IIS. Try to reproduce the error on the Ometa IIS Server to get the full error message.
Any of these errors can occur when executing a building block, method or any action within an ADM, CM, Custom component, ...
O365 TLS Deprecation & Cypher Suites
Since October 2020, Microsoft has deprecated the use of TLS 1.0 / 1.1. Mid 2021 they started to rollout updates to their servers to disable the use of TLS 1.0 and TLS 1.1 and restrict supported cypher suites.
Only the following 4 cypher suites are supported:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
Explanation
First of all, normally you'll only encounter these issues on a windows server 2008 or 2012. Starting from 2016, these issues shouldn't occur.
Depending on the security settings of your server and company policies, it can happen that newer transport security layers, like TLS 1.2, are not used by default. When this is the case, it can happen that a building block, a method or any other communication to a secured resource (like SharePoint Online) fails stating one of the errors above.
It can also happen that your server doesn't support the cypher suites required by the remote party. This is very likely to occur more and more on older windows servers (2008 & 2012) which connect to Office 365 environments.
Solution
Disable Unsecure and Force Secure Protocols
To ensure that the most secure protocol is used (TLS 1.2 atm), you can make some adjustments to the register by adding/updating various keys.
- Open the Windows Registry Editor
- Navigate to the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft.NETFramework\v4.0.30319
- Add or update the REG_DWORD named SchUseStrongCrypto and set its value to 1
- Add or update the REG_DWORD named SystemDefaultTlsVersions and set its value to 1
- Do the same for this location: HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft.NETFramework\v4.0.30319
- Restart the Ometa Services.
- Restart IIS.
Enable Support for Additional Cypher Suites
You'll need to support at least one of the cypher suites that the remote party also supports. Starting from July 2021, Microsoft only support the following 4 cypher suites:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
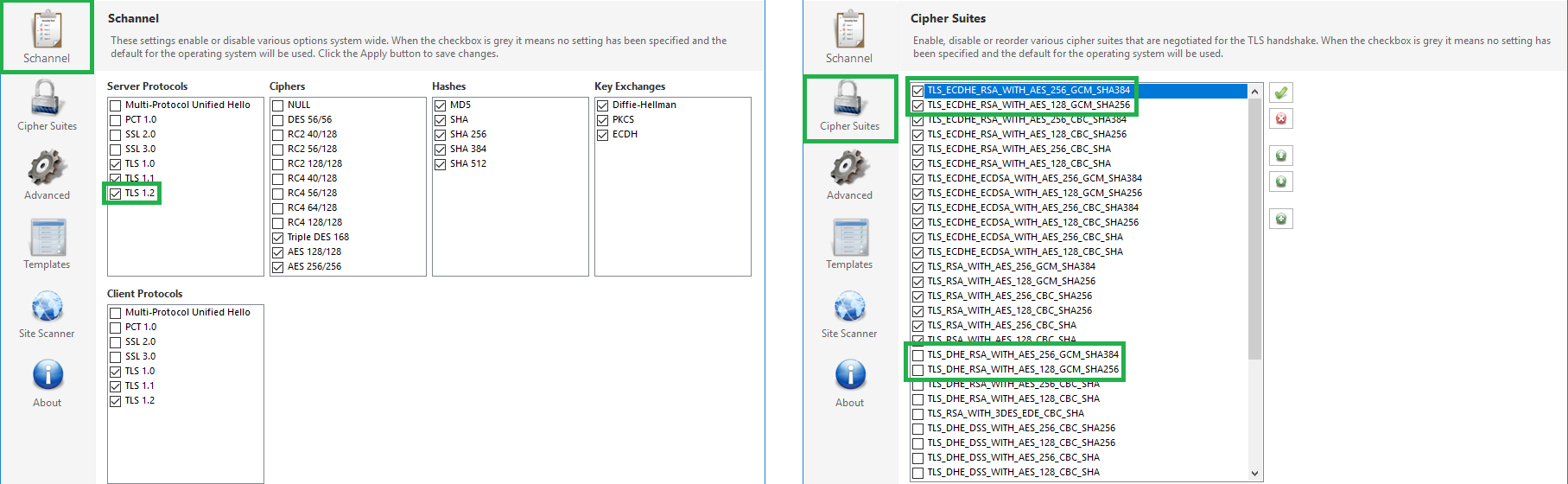
Chances are that if you have a windows server 2008 or 2012, none of the above cypher suites is supported. To resolve this issue, we temporarily make use of a tool called IISCrypto.
Download and start the IIS Crypto GUI and double check the following:
- Support for TLS 1.2 is enabled
- One of the above cypher suites is enabled (in our example 2 out of 4 are enabled)
Important
If you apply one or more changes, you'll need to reboot the server.