Windows Provider (AD) 
Due to the fact that a local AD doesn't support the OAuth 2.0 protocol, we had to customize our implementation in a way that the local AD can be used just as any other OAuth 2.0 enabled provider. Your local AD can thus be used as an authentication & claims provider. By default this provider is the only one that will be enabled if you install the security layers for the first time.
Setup
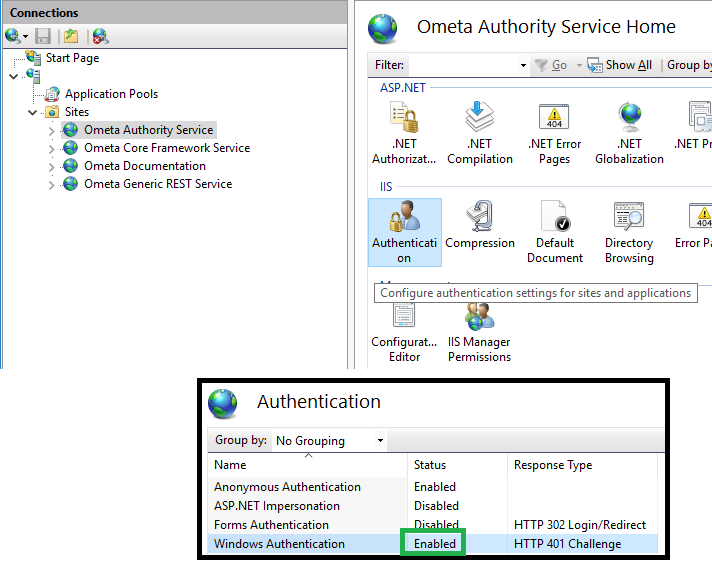
The only thing you need to do for using the local AD as a provider is ensure that Windows authentication is enabled on the Authority Service.
Claims
The following claims are provided by Windows when a user successfully authenticates itself.
- nameidentifier
- name
- givenname
- surname
- emailaddress
- adgroup (zero, one or multiple times depending on the memberships of the user)
An example:
| Type | Value |
|---|---|
| nameidentifier | OMETA\john.doe |
| name | John Doe |
| givenname | John |
| surname | Doe |
| emailaddress | john.doe@ometa.net |
| adgroup | Everyone |
| adgroup | OMETA\External |
| adgroup | OMETA\Domain Users |